Unknown Knowns
Elio Grieco
22-September-2022
Where
Talk given at 2022 Phoenix Security & Audit Conference.
Slides available at: https://eliogrieco.com/unknown-knowns/

What
A talk about older and more obscure research in cybersecurity and computer science that ought to be more widely known.
I have made this longer than usual because I have not had time to make it shorter.Why
What we’re doing today isn’t working.
“If we just dig faster, we’ll surely get out of this hole.”

Looks can be Deceiving
Hidden complexity can be a lethal danger.

Bolton Strid
What appears to be a small stream one could easily jump across hides unfathomable depths of around 65 meters.
Forgotten Principles
We seem to have forgotten some critically important rules of security.
Complexity is the enemy of Security
- Complex systems are hard to understand and reason about.
- Weird Machines arise from complexity.
- Weird Machines are the mathematical framework for understanding security vulnerabilities.
Principle of Least Access
- PoLA seems to have been renamed Zero Trust™
- Deny/Allow > Allow/Deny
- Secure defaults are important, very important
CIA Triad
A good start…
- Confidentiality
- Integrity
- Assurance
Parkerian Hexad
Some important nuance, especially in the Cloud™
- Confidentiality and Possession
- Integrity and Authenticity
- Availability and Utility
Security is NOT a people problem!
Security Without Computers
- Security is never 100%, but we had it handled pretty well before computers.
- Security in a military context goes back millennia.
- People do not have the tools needed for security in the digital world.
Identity and Trust
- Meaningful trust requires strong identity.
- Strong identity must be self-sovereign (users generate and manage their own keys).
- Keys should be endorsed by others, not managed.
- Identities must be long lived.
Trust Cures Over Time
For trust to be useful:
- Trust must be multi-path (Web of Trust)
- Trust takes a long time to build…
- But trust can be lost instantly.
Costly Trust
- Incentivizes good behavior.
- Prevents Sybil Attacks.
- Provides a form of damping.
Threat Dynamics
Why is it so hard to defend?
Scalability of Threats
- Offensive research is being deployed faster than defensive techniques.
- Fuzzing and black box testing are getting faster and easier.
- Pulling JPEGs out of thin air
Asymmetry of Threats
- Today’s attacks favor the attacker (reflection attacks).
- Properly designed systems should give the “high ground” to defenders.
- Named Data Networking (NDN) returns the advantage to the defender.
Scalability of Solutions
- Training people does not scale!
- Fixing software and using better tooling scales.
- Malcolm Harkins’ 9 Box of Controls (2016)
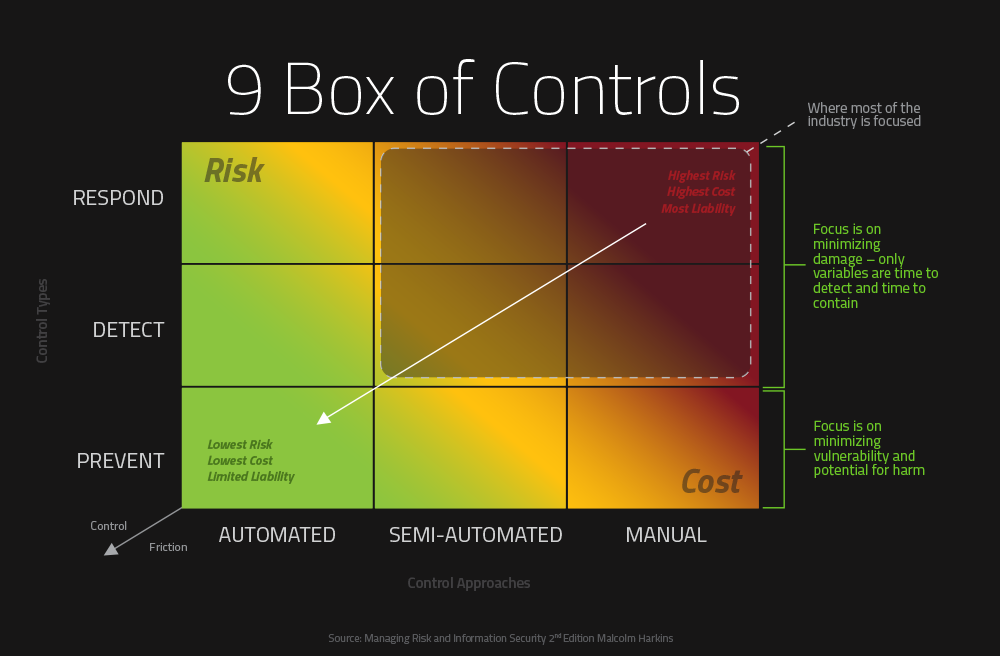
Secure Coding
It’s actually possible to write highly robust and secure code.
Learned Helplessness
Why has the software industry given up on proper engineering?
- We’ve been legally allowed to via ToS and EULAs.
- “It costs too much.” While we conveniently ignore the ever growing costs of breaches and lethal defects.
- Programmers don’t want to learn new things.
Undefined Behavior is the WORST
- Writing software is about defining a process.
- No one knows what will happen when undefined behavior is involved.
- This is an indication of complete failure.
- Code sections with undefined behavior are breaches, hacks, and disasters is waiting.
Limits of Testing
Testing can prove presence of errors, but can never prove absence of errors.
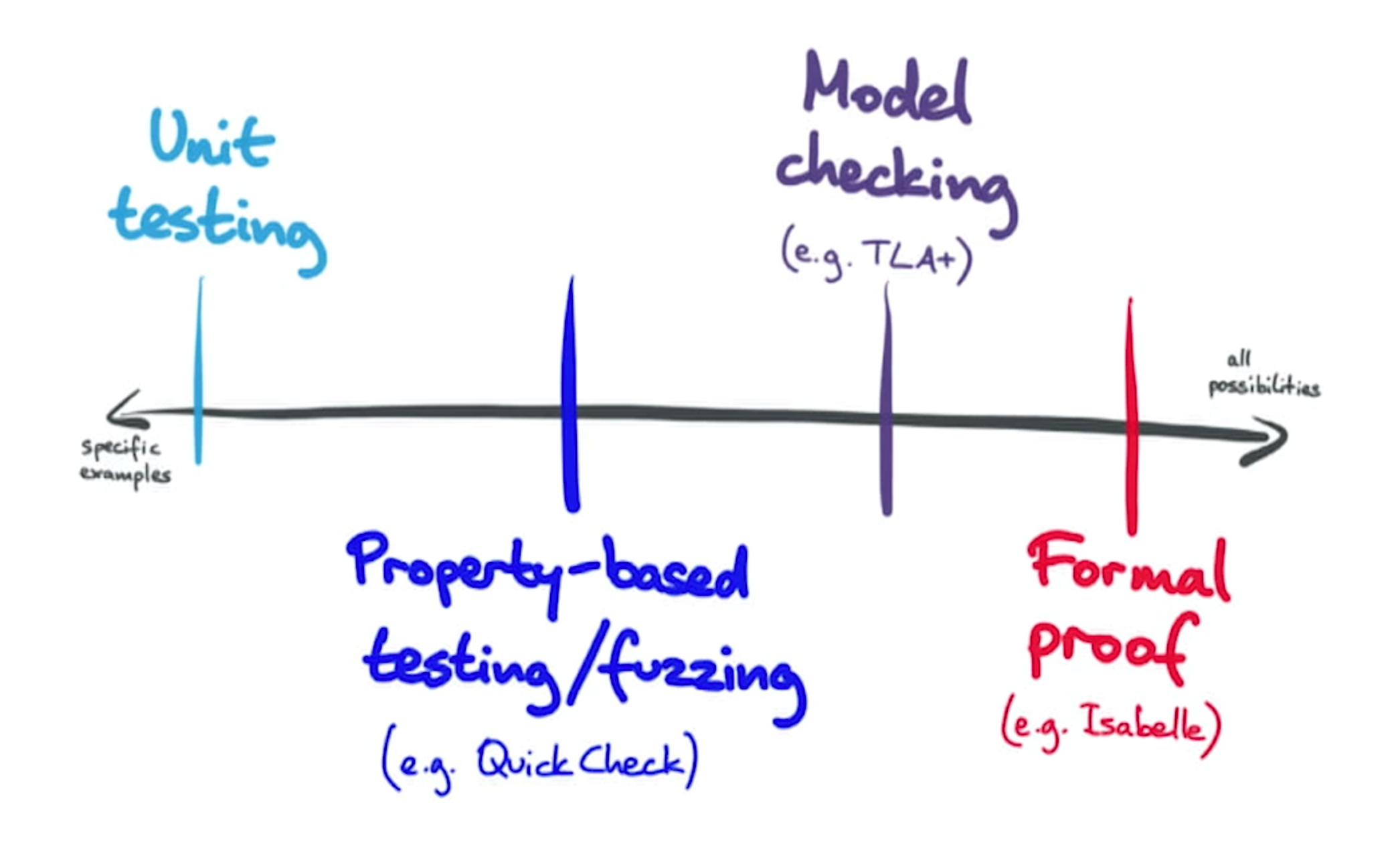
Tooling and Techniques
- Languages and tooling matter.
- Choose languages and tools that make hard things easy and impossible things possible.
- Making Software ‘Correct by Construction’ - Professor Martyn Thomas CBE
- Static/Dynamic Analysis
Code Correctness and Robustness Hierarchy
People love to put numbers on things. Here you go, a simple 1-10 scale for code correctness.
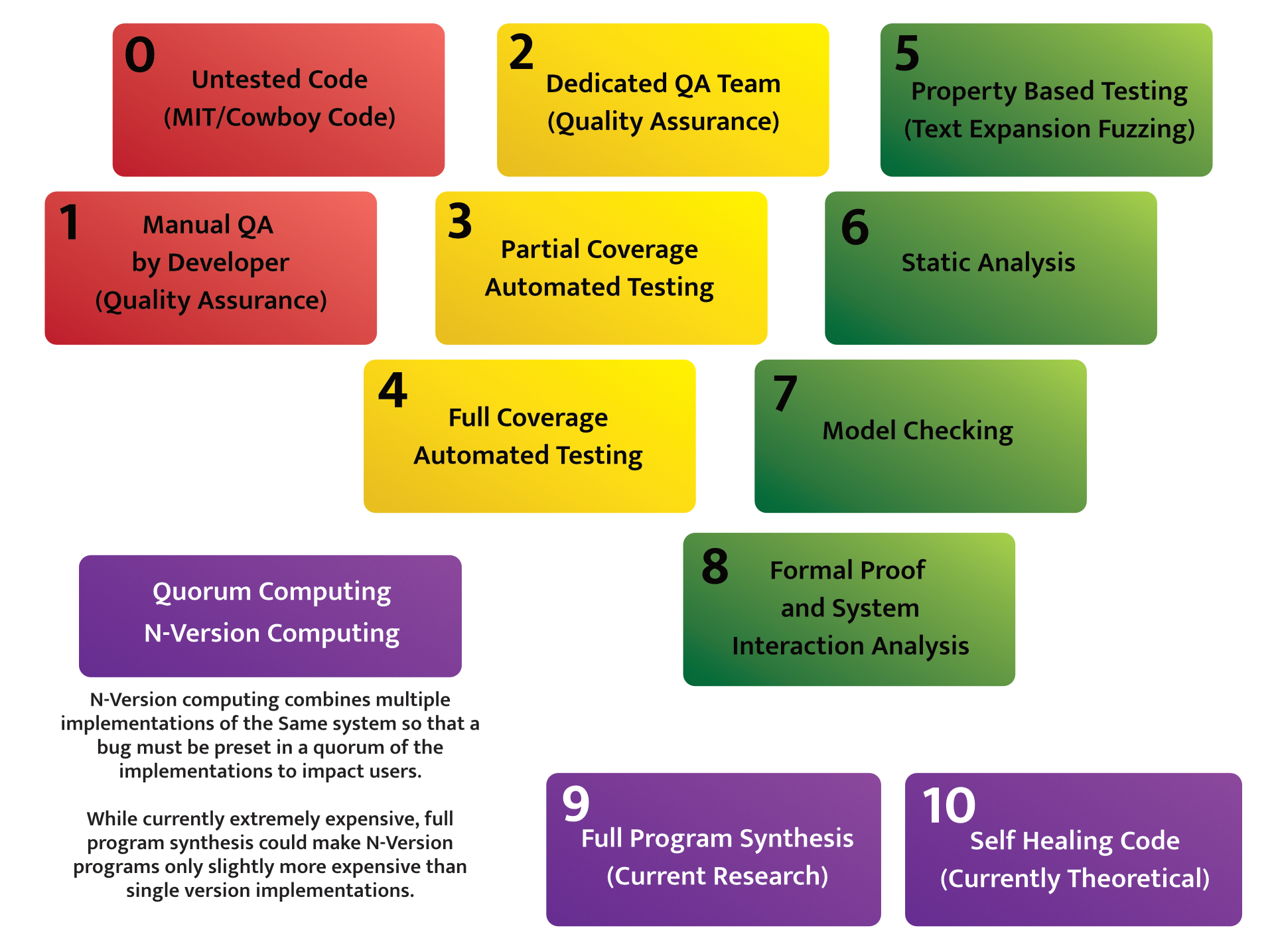

Real Security
- Language-theoretic Security
- Weird Machines
- Type systems, theorem provers, and formal methods can help us create highly robust code.
- Quorum systems (homogeneous and heterogenous) allow proper operation under extreme conditions.
Types of OSes
Cyber Defense Triad
- Limit Subversion: Subversion is tool for choice for witted adversary
- Have Mandatory Access Controls: Only label-based MAC policy can enforce secure information flow
- Have Verifiability: Security kernel (reference monitor) is only known verifiable protection technology
Finer Points of Formal Methods
- Fully defining systems is hard: Falsehoods programmers believe
- System boundary verification
- Model vs what was actually built (LVS in EDA, Ada SPARK)
Resilience via System Topology
The internet was designed to be fully decentralized.
Something Went Terribly Wrong
Today’s internet is highly centralized.
Incident: Not So Fastly: Global Outage Highlights Cloud Challenges
Why Did We De-Invent the Internet?
- Profitability
- The Feudal Internet
- Conway’s Law
Centralized Systems are Fragile
- Single points of failure
- Internal infrastructure becomes external
- Insider threats: more insiders, broader damage
- Bigger trust surfaces
Centralized Systems Lead to
- Increased fragility and incentivization of breaches.
- Loss of damping and isolation.
When everything is connected, everything is critical infrastructure.
Data is not the new Oil
A common phrase was “data is the new oil” because it is valuable, and those who process it will get rich.
Data is Plutonium
- Pile up too much plutonium and it will go critical.
- Putting data in one place incentivizes espionage and improves the economics of ransomware.
Distributed Systems are Robust
- Properly designed system boundaries provide isolation and damping
- Distributed systems generally have to be designed to be fault tolerant
Distributed Systems Challenges
- CAP Theorem and Physics
- Distributed systems must be robust to work at all.
8 Fallacies of Distributed Computing
- The network is reliable.
- Latency is zero.
- Bandwidth is infinite.
- The network is secure.
- Topology doesn’t change.
- There is one administrator.
- Transport cost is zero.
- The network is homogeneous.
Damping and Isolation
- Damping and isolation are critical to prevent or mitigate cascading failures.
- Connecting systems makes them into a larger system.
- Connecting systems allows failures to spread.
- Removing damping increases failure propagation speed and can amplify small fluctuations into bigger issues.
Knowledge Horizons
- Knowledge must be findable to be useful.
- Knowledge must not be findable by everyone.
- No single entity should see everything.
- No one should be able to see beyond their “horizon”.
Beware Magic Bullets
Don’t shoot yourself in the foot.
Limitations of ML/AI
- Supervised vs unsupervised learning
- Energy/Compute for Training
- Fuzzy and probabilistic, not explainable
- Vulnerable to poisoning, bad training data, inadequate training entropy
- It has optical illusions that are VERY different from human ones, and thus very hard to predict
- Other AI/ML threats
- AI Does not understand meaning
Blockchain
- An overrated data structure
- Poor scalability
- Handles CAP Theorem poorly
- Disadvantages of centralized and decentralized systems all at once
Anonymity and Pseudonymity
- Trust is a good thing, it is a performance optimization
- Anonymity vs Pseudonymity. Protection comes from unlinkability, not anonymity directly.
- Falsely linking people to Ashley Madison of Sanctioned Ethereum Accounts, IP address sting incident with FBI
- Recorrelational Attacks and Data Enrichment (Dr. Latanya Sweeney)
- Side channels are making it very hard to keep data private (Side Channels by Mordechai Guri et. al.)
Internet of Things (IoT)
- Increased attack surface
- Increased risk of cascading failures
- Reduced damping
- Decreased reliability